- June 22, 2020
- Category: Automation, CSV
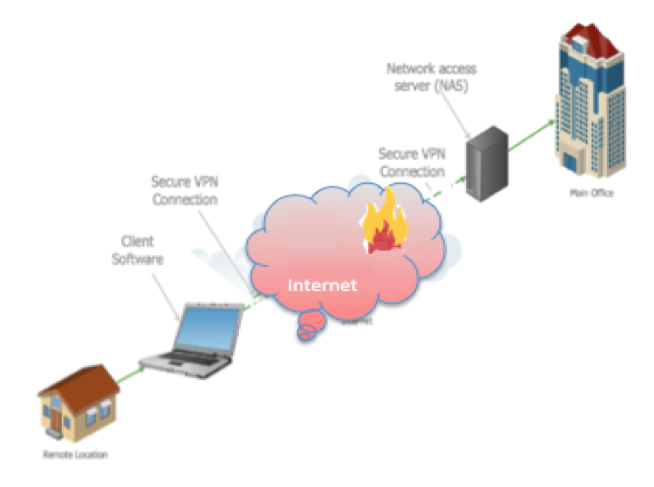
Pharmaceutical company professionals understand the necessity of maintaining schedules and deadlines. In response to the pandemic of 2020, many technologically sophisticated businesses’ IT support teams have deployed the software tools to keep us integrated with our professional communities while observing the new work from home or quarantine limitations being imposed on the workforce. This is primarily accomplished by establishing Internet based Virtual Private Networks, or “VPN”s.
The tools to accomplish this deserve some attention, since many of us are unlikely to be familiar with the details of maintaining this “connectivity”. Most of us might not require the same depth of knowledge that would be required of those in an IT department, however it behooves us to have a greater understanding of the technologies being deployed. The challenge for the optimum solution is satisfying the opposing requirements: being easy to use, providing user convenience, while at the same time, being completely secure and reliable.
The idea of accessing a company’s computer network resources remotely is not new at all, almost as old as computer networks themselves. Some readers might remember the era of dial-up modems and in some corporate settings, dedicated leased lines, where cost was deemed justified. But what is new and different now is the accessibility and affordability of these remote access solutions via the infrastructure provided by the Internet.
As its technology continues to evolve, the Internet has found its way into almost every aspect of our daily lives. Your email, text messages, YouTube, ‘the Google’; all are closer to us than the TV remote. As welcome as this is generally, it brings with it some rather unwelcome intrusion as well. Just as the telephone allowed the invention of crank or other unwanted calls, the Internet has inadvertently allowed the opportunity for malicious cybercrime activity. During this time, Virtual Private Networks have evolved to address these challenges with specific adaptations optimized for the aspects of each varying set of circumstances.
These VPNs can be categorized according to whether the implementation is an enterprise solution, usually implemented by company IT personnel, or if it’s a consumer retail package, meaning the user is implementing and managing the software themselves. The logical arrangement of the connection network, called the topology, is a further type of categorization, based on its purpose, being either a Site-to-Site or a Remote Access. Our principal focus will be VPNs used for remote access.
The user experience will largely depend upon the software architecture of the particular VPN software being used. Some VPN products are in the form of stand-alone applications, that route all outbound internet traffic to the destination end-point. Cisco AnyConnect Secure Connection is an example of this type of VPN.
From the duration of a VPN session, your every keystroke and mouse click is effectively delivered to the network location of your work location, you are – virtually speaking – at work. The entirety of your network traffic is delivered to your work node and proceeds onward, as if you were right there in the office.
Other types of VPN’s can integrate with your browser, as a browser extension. Your activity while using that VPN arrangement travels within the secure VPN tunnel, protected by VPN encryption. But in the case of a browser extension, the protection of net traffic occurs only while using that browser. However, browser based VPN software does not protect any other activity occurring separately from the browser, such as email or file transfers.
There are some VPN products that are designed as stand-alone browsers, with a particular focus on being used for remote desktop and file transfer purposes (E.G. TeamViewer). Now with the upswing in malicious web activity even in web conferencing (E.G. Zoom, WebEx, GoToMeeting, etc.), those platforms are being enhanced for improved privacy and security.
One VPN provider reported a 124% increase in VPN usage, with other VPN companies reporting similar results globally. Reports are now indicating that various Cyber Crime has increased, with Health-oriented organizations suffering the worst attacks. The world health organization is reporting a 500% increase in malicious cyber attacks on their facilities and personnel.
These descriptions span a number of different VPN products, and the readers who are within the purview of a company will probably enjoy the benefit of having a solution provided by their IT department. If your company does not provide this support or you are otherwise on your own, a resource for product selection would be found at: https://www.top10vpn.com/best-vpn-for-usa/
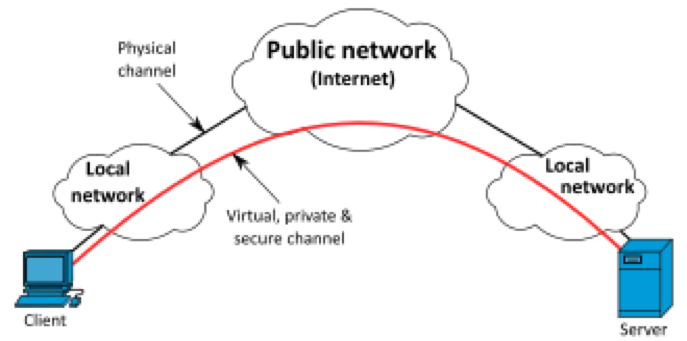
In a general sense, there is a common characteristic and architecture for any VPN. The principal being a connection that appears and behaves as a completely private communication channel, while implementing the highest degree of security that is available, while also practical. This provides the security equivalent of a single cable running the uninterrupted distance between two endpoints, while the actual details the route our data takesremains invisible.
For example, as a keystroke or other data is prepared for outbound transmission from a user’s laptop, before it is placed in the Ethernet transmit buffer, it is encrypted, thwarting any subsequent attempts at eavesdropping during message transmission. A corresponding program already running on the ‘other end’, whatever that might be, intercepts and recognizes the incoming data as encrypted VPN packets that it knows how to decrypt and pass the data onward to the operating system or other intended recipient. So every VPN, by definition, would have such an arrangement; a sender encrypting data and a receiver decrypting it. The sender’s and receiver’s roles can be reversed at any moment, as messages and their replies are required to be exchanged.
It should be mentioned that we would think the addition of encryption and decryption might be a drain on bandwidth, but that is offset by the speed improvement resulting from being on the private channel. Think of a comparison between a busy 8-lane highway, with heavy traffic, compared to a two-lane road with no other vehicles or any speed limit.
VPN Network Configuration = Topology
Virtual Private Networks quickly adapted to different circumstances and became optimized for those specific circumstances. If we take the example of an individual wishing to access the resources of a company they are authorized to access, there are the two End Points, the user and the company servers they wish to access, and the connection between the two. In the past, this might have been a dial up modem or ISDN leased lines, but these were either expensive or unreliable and cumbersome.
The Internet introduced a solution that solved both expense, convenience and reliability since the Internet is conveniently available. Since this connection is over the Internet, the encryption applied prior to sending and decryption upon receipt, maintains privacy comparable to a private cable. Since this is like a tunnel due to the applied encryption, it’s designated by the term Secure Tunnel in depictions. When the arrangement of these elements is described, the term Network Topology is used to refer to it.
These VPNs are divided into categories according to the topology they exhibit:
- Point-to-Point
- Hub-and-Spoke
- Full Mesh
- Other combination or hybrid configurations
Point-to-Point VPN Topology
Point-to-Point topology refers to individual users connected to an end point, usually a company server or network node, but it can refer to any two individual endpoints. There may be several other individual connections, each of which is another “point-to-point” connection.
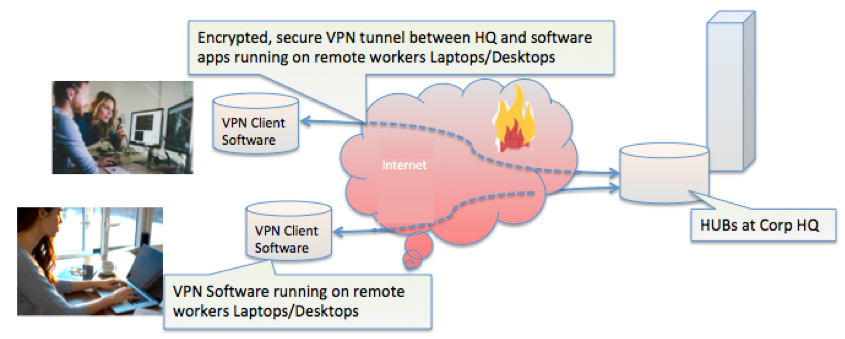
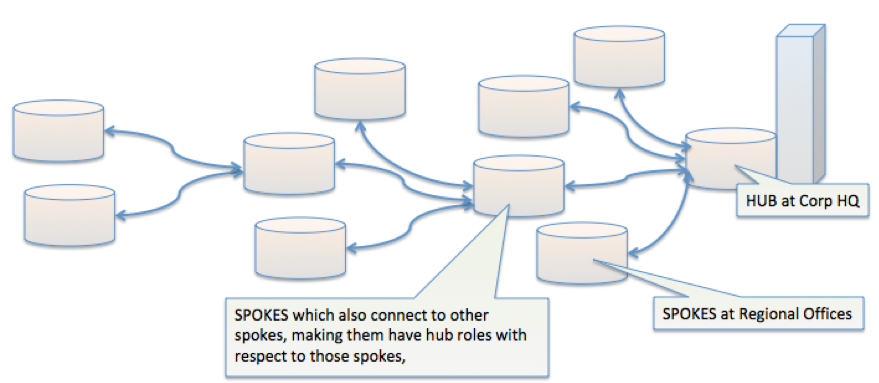
Hub-and-Spoke VPN Topology
Hub-and-Spoke topology refers to multiple branches (spokes) which are connected to a central hub. Often these includes a configuration for high availability by using a redundant solution, so no single point of failure interrupts ongoing data traffic.
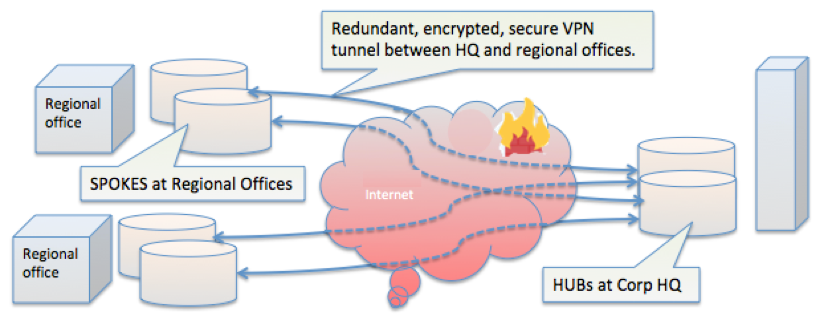
Full Mesh VPN Topology
Because of the convenience of establishing VPN channels, each business facility could, and often does, grow into a spider’s web of multiple paths, each path being secure, and directly connected (virtually, at least) to the partner it wishes to communicate with.
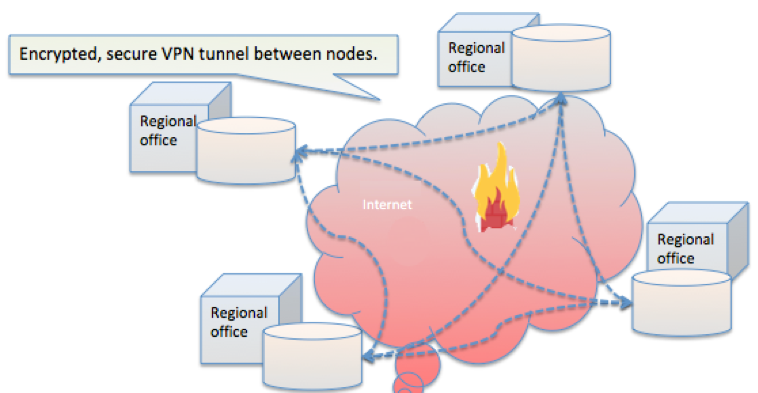
Other VPN Topologies
Many topology variations may be assembled, due to the ease of plugging in one’s Internet connection and gaining access. Often, remote users might log into a corprate location, and their credentials would then grant them access to other company locations via the established tunnels to those locations.
Under the Hood
The obvious question is how does this magic happen? This “magic”, or more precisely, this data security, can be described as consisting of a number of interdependent technologies:
Data Confidentially – like sunglasses for your data, its traveling incognito by use of symmetrical encryption via a shared private key (no public key usage). This is accomplished by the use of one of the following encryption protocols:
IPsec – Internet Protocol Security Protocol provides a very robust encryption algorithm and rigorous authentication methodology. The encryption supported is either “single DES” for 56-bit strength, or the “triple-DES” for 168-bit strength.
PPTP/MPPE – the result of an industry consortium which included the industry heavyweight, Microsoft, and includes support for multi-protocol VPNs. The MPPE is Microsoft Point-to-Point Encryption which supports either 40-bit or 128-bit strength encryptions.
L2TP/IPsec – uses the IPsec protocol with Layer 2 Tunneling Protocol (L2TP), which was a further refinement by the PPTP along with Cisco, and the Internet Engineering Task Force. Especially well suited for remote-access Windows based clients.
Data Integrity – even with the security of encryption protected data streams, there is still a case to be made for being completely certain of the authenticity of the data, both from the detection of data tampering or corruption. Every bit and bit position must match what it was upon initial transmission.
Data Origin Authentication – The sender’s identity must be rigorously verified to guard against malicious identity spoofing of legitimate senders.
Anti-Replay – The data stream is separated into packets for transmission, to make them less cumbersome to manage. Spoofing often uses the trick of sending unexpected repeat messages. This logic thwarts that attempt.
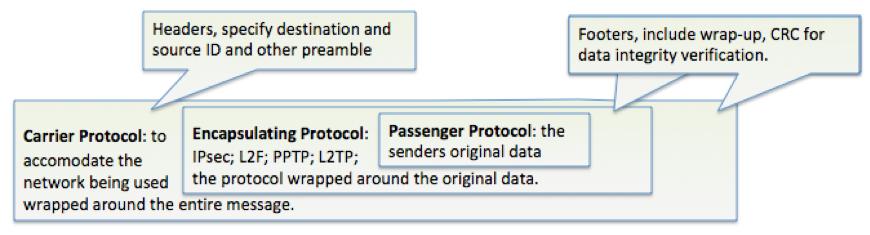
Data Tunnelling – This refers to the encapsulation of the original data by a surrounding protocol.
Authentication, Authorization and Accountability – This refers to verifying the user with known (to the VPN system only) credentials, and determining his privileges within the network. Most popular is Active Directory using LDAP (Lightweight Directory Access Protocol).
Non-repudiation – This refers to the user being held accountable for their actions, and because it was their credentials used, they cannot deny their actions.
Way Under the Hood
The internal workings of any specific VPN solution are the result of decisions and selection that has probably already been made. Some of these details deserve mention. Under the heading of the Internet Key Exchange, the IPsec peer participants negotiate IPsec encryption key establishment and exchange. The data encryption aspect of IPSec was mentioned, but details of the encryption and hash algorithms are illustrated below:
Encryption Algorithms
DES – The Data Encryption Standard uses a 56-bit key and is categorized as a symmetric key encryption algorithm. By contrast, asymmetric keys are usually more than a thousand bits in length. So while it is faster than other algorithms, it is considered to have a comparitively limited security robustness.
3DES – Triple DES is more secure since it performs three repeated passes of DES, taking the results of one DES output and repeating that process three more times. It is slow and thus consumes resources at both end-points. It should therefore not be used for video streaming from Netflix.
AES – Advanced Encryption Standard falls between DES and 3DES, being more secure that DES and more efficient that 3DES, while offering 128-Bit; 192-Bit; and 256-Bit encryption keys.
Hash Algorithms
SHA – definitely preferred, as it produces a 160-Bit digest and is more resistant to brute-force attacks than MD5. Should be used in any case requiring any medium or higher level of security.
MD5 – A popular standard for decades, produces a 128-Bit digest which sounds substantial, but has proved its weakness after being cracked by more powerful recent generation computers.
Summary
A company will select a VPN solution based on a number of factors, but for our purpose, the remote desktop and data integrity with rigorous authentication will be paramount concerns that a VPN solution must address. Data, keystrokes, mouse clicks and other data can be exchanged with a nearly 100% certainty of complete privacy, data security and integrity, as well as the authenticity of the sender. The result is maintaining a reasonable continuity of operation and information in this recent shift we have experienced on a national and global scale.

Written By
John Andrews
Director of Automation

